Navigating the New DOGE Impacted FDA: How MedTech Companies Can Build a Competitive Advantage
The Center for Devices and Radiological Health (CDRH) is a key branch of the FDA that is responsible for ensuring the safety and effectiveness of medical devices. Companies interact with the CDRH through premarket submissions, quality inspections, recalls, and a variety of other activities.
In 2025, the Department of Government Efficiency (DOGE) was established to streamline federal operations, reduce redundancy, and improve cost-effectiveness across agencies. While its goals are rooted in efficiency, the implementation has led to substantial structural and operational shifts that will have a profound impact on the industry.
For companies developing medical devices, understanding these changes is essential for navigating the evolving regulatory landscape. This blog will help you learn all about those changes and provide actionable strategies to stand above the competition while navigating the new frontier.
Key Changes to CDRH Under DOGE
One of the most immediate and highly publicized impacts has been a reduction in staffing. The CDRH has experienced layoffs, hiring freezes, and a mandated attrition ratio. These changes have affected teams working on new technologies, slowing down review processes and resulting in a reduction in internal expertise.
Budget and Operational Adjustments
DOGE reforms have also reduced discretionary funding, increasing the CDRH’s reliance on user fees from industry sponsors. This shift has created operational bottlenecks, particularly in areas not directly supported by these fees, such as early-stage innovation and public health initiatives.
Regulatory Process Reforms
With fewer staff and resources, the CDRH has had to adjust some of its regulatory workflows. It has been reported that pre-submission meetings are less frequent, and review timelines have lengthened. While the agency remains committed to scientific rigor, the capacity to provide interactive feedback has diminished.
RELATED: Jama Connect® for Medical Device & Life Sciences Development Datasheet
Strategic Reforms Planned for the CDRH
Proposed Guidance Still Moving Forward
Despite the challenges mentioned above, CDRH plans to continue advancing its strategic priorities. The FDA has released its 2025 guidance agenda which includes the following amongst a larger list of items:
- Cybersecurity in Medical Devices: Updated guidance on quality system considerations and premarket submissions.
- AI Lifecycle Management and Change Control Plans: Recommendations for predetermined change control plans.
- Use of Real-World Evidence in Regulatory Decisions: Revised guidance to support regulatory decision-making.
- Updated Q-Submission Program Guidelines: Updates to improve feedback and meeting processes for device submissions.
These initiatives reflect CDRH’s ongoing commitment to modernization, even amid structural constraints resulting from DOGE actions.
AI Use in Submissions: A New Frontier
In another move to improve efficiency and modernize the agency, the FDA has begun using Elsa, a generative AI tool to assist in the scientific review of medical device submissions. This tool will help automate repetitive tasks such as document parsing and data extraction, allowing human reviewers to focus on more complex portions during the evaluation. The rollout is expected to be complete by mid-2025, with early results showing promise in reducing review times and improving consistency.
Proven Strategies for Navigating the Changes
For those in the medical device industry, these changes present both challenges and opportunities. Companies that embrace the changes and take a proactive approach to interacting with the FDA will find themselves at the forefront of the new era.
Here are some key approaches to consider:
- Prioritize Proactive Regulatory Planning: A clear and complete regulatory plan is a vital piece of every new product development project. It will be especially important now as you should prepare for longer review times and less interaction with reviewers. Build extra time for regulatory approvals and work with regulatory consultants to anticipate and address obstacles.
- Maintain Clear Communication with the FDA: Given the FDA’s reduction in resources, clear and targeted communication is more important than ever. Leveraging the FDA’s pre-submission program allows you to gain valuable insights early in the submission process. Regular interaction will help build rapport with the agency while addressing concerns before they delay approvals.
- Collaborate Across Teams to Document All Product-Related Information: Interdepartmental alignment is critical when interacting with the FDA. Your product development, QARA, and manufacturing teams must communicate effectively to address compliance needs and streamline decision-making. Working together to tell a cohesive and complete story about your device will be imperative when interacting with reviewers. It will be especially important in the future as AI tools may flag inconsistencies or gaps more rigorously than human reviewers.
- Leverage Digital Transformation: Investing in digital tools is no longer optional for medical device product development teams. Modern platforms help teams track requirements, manage testing, and maintain documentation seamlessly. Digital platforms also ensure traceability, streamlining compliance audits, and reducing risks of regulatory missteps. Additionally, automated workflows and AI-powered solutions can reduce manual effort and free up critical resources to do what they do best, designing life-changing technologies.
RELATED: Buyer’s Guide: Selecting a Requirements Management and Traceability Solution for Medical Device & Life Sciences
How Jama Software Can Support Your Success
When navigating regulatory pressures, Jama Software is the trusted partner MedTech companies need. Our platform empowers organizations to overcome compliance challenges while maximizing efficiency. Here’s how Jama Connect will help you navigate the changes at the FDA:
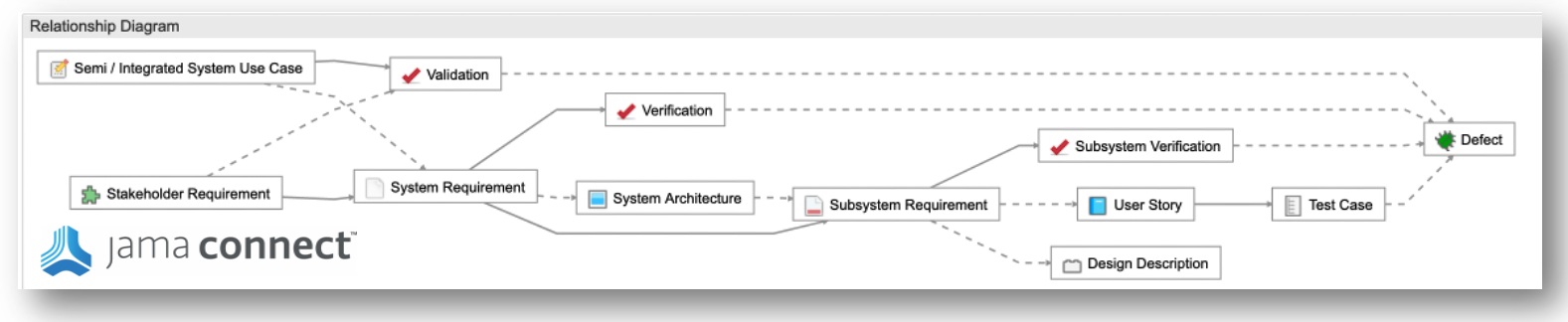
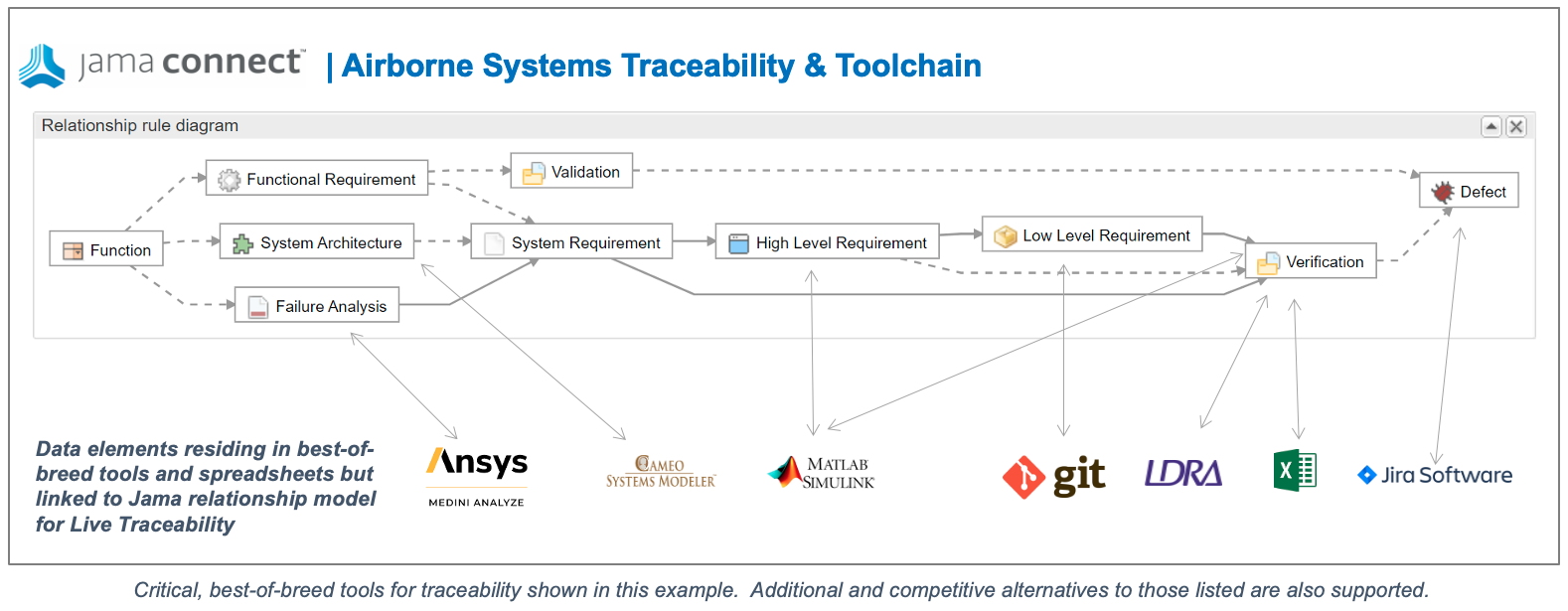
- Simplify Regulatory Compliance: Jama Connect® simplifies compliance with FDA regulations by providing complete traceability throughout product development. Built-in templates for ISO 13485, ISO 14971, and FDA requirements help teams comply effortlessly with the regulations.
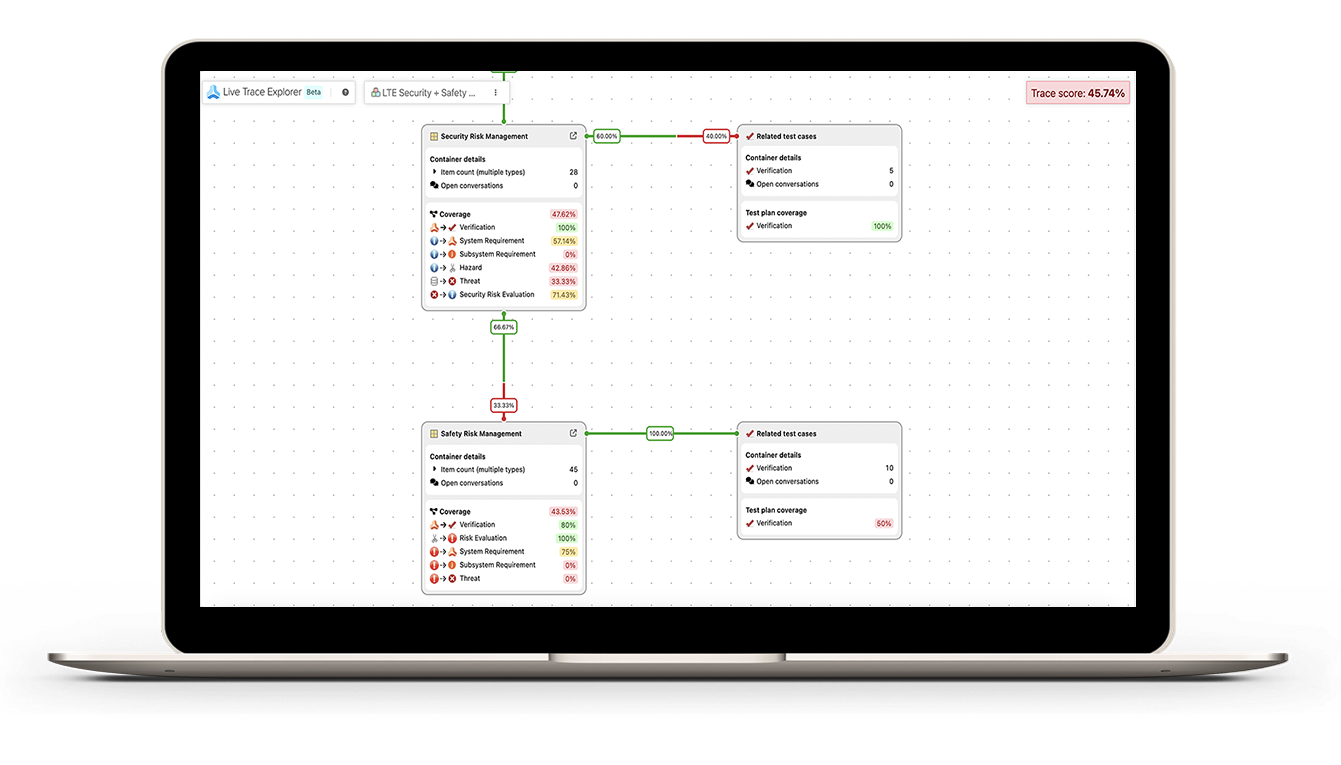
- Reduce Submission Errors: Errors in FDA submissions can lead to costly delays and loss of potential revenue. Jama Software’s traceability matrix ensures all requirements are accounted for and verified, reducing the likelihood of mistakes that can delay review times or even result in resubmissions.
- Accelerate Time-to-Market: Our real-time collaboration and requirement management tools optimize project workflows, reducing rework and enabling faster decisions. This means your products reach the market sooner, even when facing FDA review delays.
- Improve Risk Management: With Jama Connect’s risk management capabilities, teams can capture failure modes and hazard analyses for medical devices, ensuring adherence to safety requirements under FDA guidelines.
- Stay Aligned Across Teams: Jama Connect’s centralized platform fosters alignment between engineers, designers, and quality assurance teams. Eliminate silos, improve team collaboration, and keep every stakeholder fully informed at all stages of development.
- Create a Competitive Advantage in the New Era of MedTech: The DOGE-era FDA brings unprecedented change to the MedTech industry. With the right strategies and tools, your organization can turn these challenges into opportunities to build resilience, operational efficiency, and create a competitive edge.
To streamline product development, tackle complex compliance requirements, and stay ahead in the fast-evolving MedTech landscape, consider partnering with Jama Software. Curious how Jama Software can help your team thrive? Learn More Today.