What is DevSecOps? A Guide to Building Secure Software
The Essential Guide to Requirements Management and Traceability
Chapters
- 1. Requirements Management
- Overview
- 1 What is Requirements Management?
- 2 Why do you need Requirements Management?
- 3 Four Stages of Requirements Management Processes
- 4 Adopting an Agile Approach to Requirements Management
- 5 Status Request Changes
- 6 Conquering the 5 Biggest Challenges of Requirements Management
- 7 Three Reasons You Need a Requirements Management Solution
- 8 Guide to Poor Requirements: Identify Causes, Repercussions, and How to Fix Them
- 2. Writing Requirements
- Overview
- 1 Functional requirements examples and templates
- 2 Identifying and Measuring Requirements Quality
- 3 How to write system requirement specification (SRS) documents
- 4 The Fundamentals of Business Requirements: Examples of Business Requirements and the Importance of Excellence
- 5 Adopting the EARS Notation to Improve Requirements Engineering
- 6 Jama Connect Advisor™
- 7 Frequently Asked Questions about the EARS Notation and Jama Connect Advisor™
- 8 How to Write an Effective Product Requirements Document (PRD)
- 9 Functional vs. Non-Functional Requirements
- 10 What Are Nonfunctional Requirements and How Do They Impact Product Development?
- 11 Characteristics of Effective Software Requirements and Software Requirements Specifications (SRS)
- 12 8 Do’s and Don’ts for Writing Requirements
- 3. Requirements Gathering and Management Processes
- Overview
- 1 Requirements Engineering
- 2 Requirements Analysis
- 3 A Guide to Requirements Elicitation for Product Teams
- 4 Requirements Gathering Techniques for Agile Product Teams
- 5 What is Requirements Gathering in Software Engineering?
- 6 Defining and Implementing a Requirements Baseline
- 7 Managing Project Scope — Why It Matters and Best Practices
- 8 How Long Do Requirements Take?
- 9 How to Reuse Requirements Across Multiple Products
- 4. Requirements Traceability
- Overview
- 1 How is Traceability Achieved? A Practical Guide for Engineers
- 2 What is Requirements Traceability? Importance Explained
- 3 Tracing Your Way to Success: The Crucial Role of Traceability in Modern Product and Systems Development
- 4 Change Impact Analysis (CIA): A Short Guide for Effective Implementation
- 5 What is Meant by Version Control?
- 6 What is Requirements Traceability and Why Does It Matter for Product Teams?
- 7 Key Traceability Challenges and Tips for Ensuring Accountability and Efficiency
- 8 The Role of a Data Thread in Product and Software Development
- 9 Unraveling the Digital Thread: Enhancing Connectivity and Efficiency
- 10 Requirements Traceability Matrix (RTM): Definition and Purpose
- 11 How to Create and Use a Requirements Traceability Matrix (RTM)
- 12 Traceability Matrix 101: Why It’s Not the Ultimate Solution for Managing Requirements
- 13 Live Traceability vs. After-the-Fact Traceability
- 14 Overcoming Barriers to Live Requirements Traceability™
- 15 Requirements Traceability, What Are You Missing?
- 16 Four Best Practices for Requirements Traceability
- 17 Requirements Traceability: Links in the Chain
- 18 What Are the Benefits of End-to-End Traceability During Product Development?
- 19 FAQs About Requirements Traceability
- 5. Requirements Management Tools and Software
- Overview
- 1 Selecting the Right Requirements Management Tools and Software
- 2 Why Investing in Requirements Management Software Makes Business Sense During an Economic Downturn
- 3 Why Word and Excel Alone is Not Enough for Product, Software, and Systems Development
- 4 Application lifecycle management (ALM)
- 5 Is There Life After DOORS®?
- 6 Can You Track Requirements in Jira?
- 7 Checklist: Selecting a Requirements Management Tool
- 6. Requirements Validation and Verification
- 7. Meeting Regulatory Compliance and Industry Standards
- Overview
- 1 Understanding ISO Standards
- 2 Understanding ISO/IEC 27001: A Guide to Information Security Management
- 3 What is DevSecOps? A Guide to Building Secure Software
- 4 Compliance Management
- 5 What is FMEA? Failure Modes and Effects Analysis
- 6 TÜV SÜD: Ensuring Safety, Quality, and Sustainability Worldwide
- 8. Systems Engineering
- Overview
- 1 What is Systems Engineering?
- 2 How Do Engineers Collaborate? A Guide to Streamlined Teamwork and Innovation
- 3 The Systems Engineering Body of Knowledge (SEBoK)
- 4 What is MBSE? Model-Based Systems Engineering Explained
- 5 Digital Engineering Between Government and Contractors
- 6 Digital Engineering Tools: The Key to Driving Innovation and Efficiency in Complex Systems
- 9. Automotive Development
- 10. Medical Device & Life Sciences Development
- Overview
- 1 The Importance of Benefit-Risk Analysis in Medical Device Development
- 2 Software as a Medical Device: Revolutionizing Healthcare
- 3 What’s a Design History File, and How Are DHFs Used by Product Teams?
- 4 Navigating the Risks of Software of Unknown Pedigree (SOUP) in the Medical Device & Life Sciences Industry
- 5 What is ISO 13485? Your Comprehensive Guide to Compliant Medical Device Manufacturing
- 6 What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
- 7 ISO 13485 vs ISO 9001: Understanding the Differences and Synergies
- 8 Failure Modes, Effects, and Diagnostic Analysis (FMEDA) for Medical Devices: What You Need to Know
- 9 Embracing the Future of Healthcare: Exploring the Internet of Medical Things (IoMT)
- 11. Aerospace & Defense Development
- 12. Architecture, Engineering, and Construction (AEC industry) Development
- 13. Industrial Manufacturing & Machinery, Automation & Robotics, Consumer Electronics, and Energy
- 14. Semiconductor Development
- 15. AI in Product Development
- Glossary
Chapter 7: What is DevSecOps? A Guide to Building Secure Software
Chapters
- 1. Requirements Management
- Overview
- 1 What is Requirements Management?
- 2 Why do you need Requirements Management?
- 3 Four Stages of Requirements Management Processes
- 4 Adopting an Agile Approach to Requirements Management
- 5 Status Request Changes
- 6 Conquering the 5 Biggest Challenges of Requirements Management
- 7 Three Reasons You Need a Requirements Management Solution
- 8 Guide to Poor Requirements: Identify Causes, Repercussions, and How to Fix Them
- 2. Writing Requirements
- Overview
- 1 Functional requirements examples and templates
- 2 Identifying and Measuring Requirements Quality
- 3 How to write system requirement specification (SRS) documents
- 4 The Fundamentals of Business Requirements: Examples of Business Requirements and the Importance of Excellence
- 5 Adopting the EARS Notation to Improve Requirements Engineering
- 6 Jama Connect Advisor™
- 7 Frequently Asked Questions about the EARS Notation and Jama Connect Advisor™
- 8 How to Write an Effective Product Requirements Document (PRD)
- 9 Functional vs. Non-Functional Requirements
- 10 What Are Nonfunctional Requirements and How Do They Impact Product Development?
- 11 Characteristics of Effective Software Requirements and Software Requirements Specifications (SRS)
- 12 8 Do’s and Don’ts for Writing Requirements
- 3. Requirements Gathering and Management Processes
- Overview
- 1 Requirements Engineering
- 2 Requirements Analysis
- 3 A Guide to Requirements Elicitation for Product Teams
- 4 Requirements Gathering Techniques for Agile Product Teams
- 5 What is Requirements Gathering in Software Engineering?
- 6 Defining and Implementing a Requirements Baseline
- 7 Managing Project Scope — Why It Matters and Best Practices
- 8 How Long Do Requirements Take?
- 9 How to Reuse Requirements Across Multiple Products
- 4. Requirements Traceability
- Overview
- 1 How is Traceability Achieved? A Practical Guide for Engineers
- 2 What is Requirements Traceability? Importance Explained
- 3 Tracing Your Way to Success: The Crucial Role of Traceability in Modern Product and Systems Development
- 4 Change Impact Analysis (CIA): A Short Guide for Effective Implementation
- 5 What is Meant by Version Control?
- 6 What is Requirements Traceability and Why Does It Matter for Product Teams?
- 7 Key Traceability Challenges and Tips for Ensuring Accountability and Efficiency
- 8 The Role of a Data Thread in Product and Software Development
- 9 Unraveling the Digital Thread: Enhancing Connectivity and Efficiency
- 10 Requirements Traceability Matrix (RTM): Definition and Purpose
- 11 How to Create and Use a Requirements Traceability Matrix (RTM)
- 12 Traceability Matrix 101: Why It’s Not the Ultimate Solution for Managing Requirements
- 13 Live Traceability vs. After-the-Fact Traceability
- 14 Overcoming Barriers to Live Requirements Traceability™
- 15 Requirements Traceability, What Are You Missing?
- 16 Four Best Practices for Requirements Traceability
- 17 Requirements Traceability: Links in the Chain
- 18 What Are the Benefits of End-to-End Traceability During Product Development?
- 19 FAQs About Requirements Traceability
- 5. Requirements Management Tools and Software
- Overview
- 1 Selecting the Right Requirements Management Tools and Software
- 2 Why Investing in Requirements Management Software Makes Business Sense During an Economic Downturn
- 3 Why Word and Excel Alone is Not Enough for Product, Software, and Systems Development
- 4 Application lifecycle management (ALM)
- 5 Is There Life After DOORS®?
- 6 Can You Track Requirements in Jira?
- 7 Checklist: Selecting a Requirements Management Tool
- 6. Requirements Validation and Verification
- 7. Meeting Regulatory Compliance and Industry Standards
- Overview
- 1 Understanding ISO Standards
- 2 Understanding ISO/IEC 27001: A Guide to Information Security Management
- 3 What is DevSecOps? A Guide to Building Secure Software
- 4 Compliance Management
- 5 What is FMEA? Failure Modes and Effects Analysis
- 6 TÜV SÜD: Ensuring Safety, Quality, and Sustainability Worldwide
- 8. Systems Engineering
- Overview
- 1 What is Systems Engineering?
- 2 How Do Engineers Collaborate? A Guide to Streamlined Teamwork and Innovation
- 3 The Systems Engineering Body of Knowledge (SEBoK)
- 4 What is MBSE? Model-Based Systems Engineering Explained
- 5 Digital Engineering Between Government and Contractors
- 6 Digital Engineering Tools: The Key to Driving Innovation and Efficiency in Complex Systems
- 9. Automotive Development
- 10. Medical Device & Life Sciences Development
- Overview
- 1 The Importance of Benefit-Risk Analysis in Medical Device Development
- 2 Software as a Medical Device: Revolutionizing Healthcare
- 3 What’s a Design History File, and How Are DHFs Used by Product Teams?
- 4 Navigating the Risks of Software of Unknown Pedigree (SOUP) in the Medical Device & Life Sciences Industry
- 5 What is ISO 13485? Your Comprehensive Guide to Compliant Medical Device Manufacturing
- 6 What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
- 7 ISO 13485 vs ISO 9001: Understanding the Differences and Synergies
- 8 Failure Modes, Effects, and Diagnostic Analysis (FMEDA) for Medical Devices: What You Need to Know
- 9 Embracing the Future of Healthcare: Exploring the Internet of Medical Things (IoMT)
- 11. Aerospace & Defense Development
- 12. Architecture, Engineering, and Construction (AEC industry) Development
- 13. Industrial Manufacturing & Machinery, Automation & Robotics, Consumer Electronics, and Energy
- 14. Semiconductor Development
- 15. AI in Product Development
- Glossary
What is DevSecOps?
DevSecOps has gained popularity as a secure and dependable software development methodology in the fast-paced world of software development. But what is DevSecOps really, and why is it so crucial?
DevOps is a set of techniques that stresses collaboration and automation between development and operations teams. DevSecOps is the integration of security practices into this methodology. DevSecOps seeks to establish a security culture that guarantees the software is secure and complies with compliance standards by integrating security into every phase of the software development lifecycle, from planning through deployment.
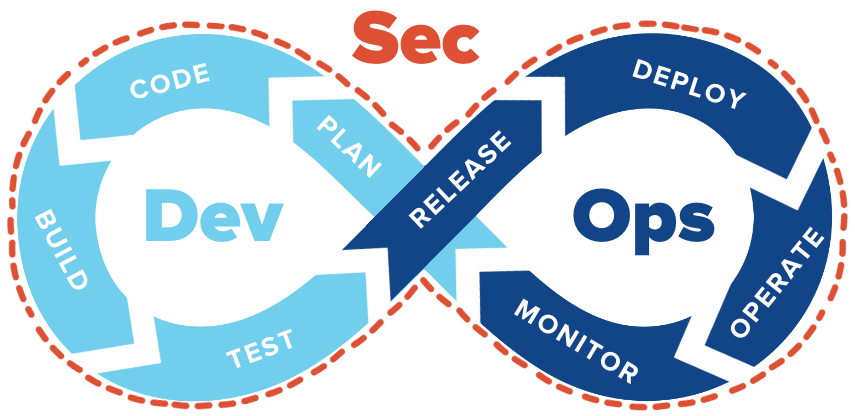
What are the advantages of DevSecOps?
The ability to identify and address security risks earlier in the development process is one of the main advantages of DevSecOps. This means that security is incorporated into the software at the outset instead of being added later, which can be expensive and time-consuming. Also, DevSecOps plays a big role in decreased risk of security breaches and data leaks by identifying vulnerabilities earlier.
The fact that DevSecOps helps to ensure compliance with laws and standards is another crucial feature of the practice. In many businesses, especially those that deal with sensitive or private data, including healthcare and banking, compliance is becoming more and more crucial. DevSecOps aids in ensuring that the software complies with requirements by incorporating compliance into the development process.
How does DevSecOps work?
What does DevSecOps look like in practice? DevSecOps is fundamentally about cooperation and communication between teams working on development, security, and operations. This implies that everyone bears some kind of responsibility for security, not just the security team. Instead of adding security features later, development teams collaborate with security and operations teams to incorporate security into the software from the start.
The automation of DevSecOps is a crucial element. Automation makes the development process more efficient, reduces errors, and ensures consistency. DevSecOps can aid in the quicker and more precise detection of vulnerabilities and threats by automating security testing and other security operations.
Ongoing monitoring with DevSecOps
Continuous monitoring is a key component of DevSecOps. This means that maintaining security involves ongoing monitoring and improvement rather than being a one-time action. DevSecOps can assist in identifying and mitigating risks before they turn into significant concerns by continuously monitoring the program for security threats and vulnerabilities.
DevSecOps also depends on a culture that values security. As a result, security is more than just a collection of guidelines; it’s also a way of thinking and conducting business. Organizations may ensure that security is always a top priority and that everyone is aware of the significance of security in their work by developing a culture of security.
DevSecOps is a vital method of software development that places an emphasis on teamwork, automation, and constant monitoring. DevSecOps contributes to the creation of a security culture that guarantees the software is secure and complies with regulatory standards by integrating security into every phase of the software development lifecycle. Organizations that implement DevSecOps are well-positioned to produce secure and dependable software that satisfies the needs of their stakeholders and customers given the growing relevance of security in today’s society.
There are numerous online resources, like blogs, podcasts, and online courses, that you may use to learn more about DevSecOps. In the world of DevSecOps, there is something for everyone, whether you are a developer, security expert, or operations specialist.
Note: This article was drafted with the aid of AI. Additional content, edits for accuracy, and industry expertise by McKenzie Jonsson.
In This Webinar, We Cover Best Practices for Requirements Traceability
DevSecOps seeks to establish a security culture that guarantees the software is secure and complies with compliance standards by integrating security into every phase of the software development lifecycle, from planning through deployment.
Book a Demo
See Jama Connect in Action!
Our Jama Connect experts are ready to guide you through a personalized demo, answer your questions, and show you how Jama Connect can help you identify risks, improve cross-team collaboration, and drive faster time to market.
