In part 1 of this 2-part blog series, we overview our eBook, “A Guide to Road Vehicle Cybersecurity According to ISO 21434” – Click HERE for part 2.
To read the entire eBook, click HERE.
A Guide to Road Vehicle Cybersecurity: Part 1
As the automotive industry becomes more complex and more connected, cybersecurity is emerging as a major concern, and therefore a priority for development teams.
One standard, in particular, has been developed to address cybersecurity risks in the design and development of car electronics — ISO SAE 21434 “Road vehicles — Cybersecurity Engineering.”
In this guide, we cover:
- An overview of ISO SAE 21434
- The urgency behind automotive cybersecurity
- How Jama Connect® supports cybersecurity engineering
Introduction
As the automotive industry becomes more complex, and more connected, cybersecurity is emerging as a major concern, and therefore priority, for development teams.
While vehicles have been traditionally isolated systems that had to be physically accessed to tamper with, increasingly, more and more vehicles include wireless connectivity. According to Juniper Research, the number of vehicles with wireless connectivity will rise from 110 million in 2020 to an excess of 200 million by 2025. These vehicles pose a much greater cybersecurity risk than previous designs.
One standard in particular has been developed to address cybersecurity risks in the design and development of car electronics – ISO SAE 21434 “Road vehicles — Cybersecurity Engineering.”
In this guide, we will examine this important automotive cybersecurity standard, how it is impacting automotive development, and lastly how Jama Software® can help.
What is Automotive Cybersecurity?
Cybersecurity, within the context of road vehicles, is the protection of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation.
What is ISO 21434?
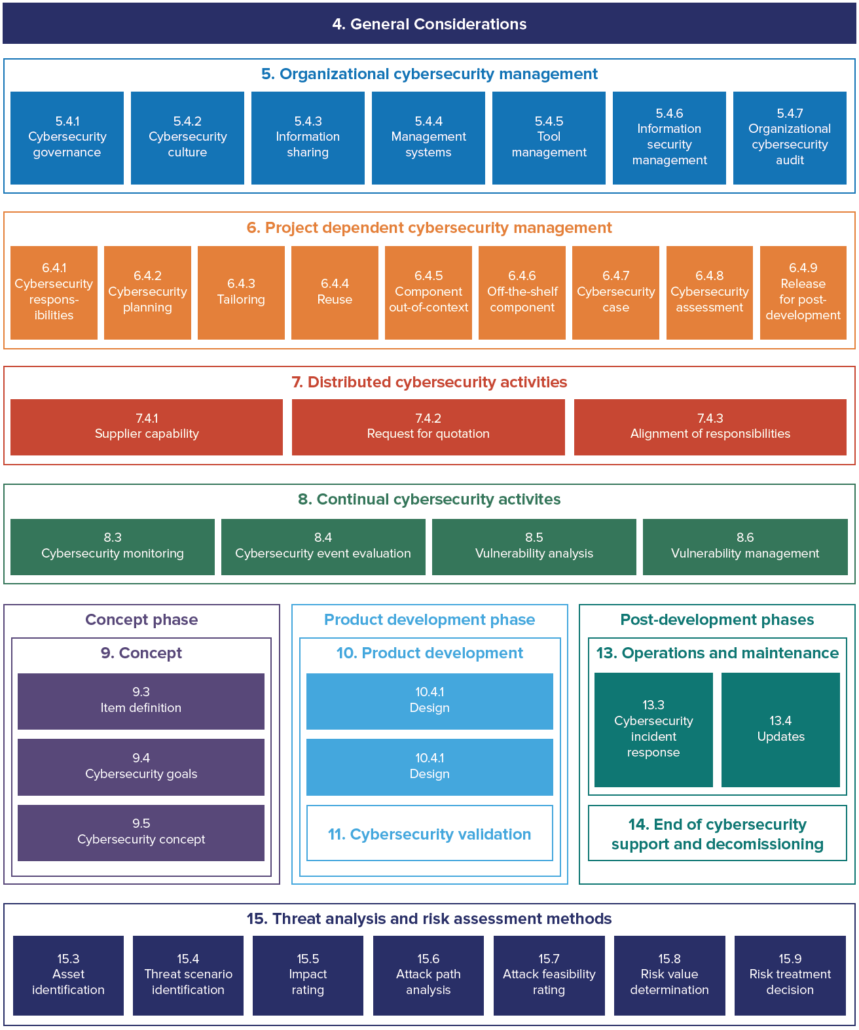
Regarded as one of the most comprehensive approaches to connected vehicle cybersecurity, ISO 21434 specifies engineering requirements for cybersecurity risk management regarding concept, product development, production, operation, maintenance, and decommissioning of electrical and electronic (E/E) systems in road vehicles, including their components and interfaces.
This standard supports the implementation of a Cybersecurity Management System (CSMS).
The first edition of ISO 21434 was published in 2021 and automotive suppliers and OEMs should strongly consider integrating ISO 21434 into their current process.
What is a Cybersecurity Management System (CSMS)?
A Cybersecurity Management System is a systematic risk-based approach defining organizational rules and processes, security policies, resources, and responsibilities to manage risk associated with cyber threats to vehicle road users and protect them from cyber-attacks.
RELATED: Best Practices to Accelerate Your Automotive Spice (ASPICE) Capabilities
ISO 21434 Standard Overview
ISO 21434 provides vocabulary, objectives, requirements, and guidelines for cybersecurity engineering in the context of electrical and electronic systems within road vehicles. The goal of the standard is to enable the engineering of electrical and electronic systems to keep up with the state-of-the-art technology and evolving cybersecurity attack methods. Adhering to the standard will allow organizations to define cybersecurity policies and processes, develop a cybersecurity culture, and manage cybersecurity risk.
The structure of the standard is as follows:
- 14 clauses, 11 are normative
- Similar structure and vocabulary as ISO 26262
- Each clause has at least one requirement and one work product
- Some clauses have RC (recommendations), and PC (permissions)
- Nine informative appendixes
Terminology
To achieve the goal of a common vocabulary within cybersecurity engineering for road vehicles, ISO 21434 defines a number of terms.
Asset: A part of an item that has cybersecurity properties (ex: OBD II port, safety requirements)
Attack Path: A series of steps that an intruder could use to compromise an asset
Cybersecurity Goal: Top level product requirement resulting from the TARA (see below for TARA definition)
Cybersecurity Claim: An identified risk that will be accepted, typically mitigated by liability transfer
Cybersecurity Concept: Cybersecurity requirements on the item and operating environment that implement controls to protect against threats
Damage Scenario: The potential damage to a road user caused by the realization of a threat scenario
Item: A component or a set of components that implements a function at the vehicle level. Could be identical to the functional safety item
TARA: Threat and Risk Assessment. Assets with cybersecurity properties are identified and damage scenarios are identified if the asset is compromised. Threat scenarios are identified and supported with attack paths. Risk values are assigned, and cybersecurity goals are established for unacceptable risk
Threat Scenario: Potential cause of the compromise of the cybersecurity properties of one or more assets that leads to a damage scenario
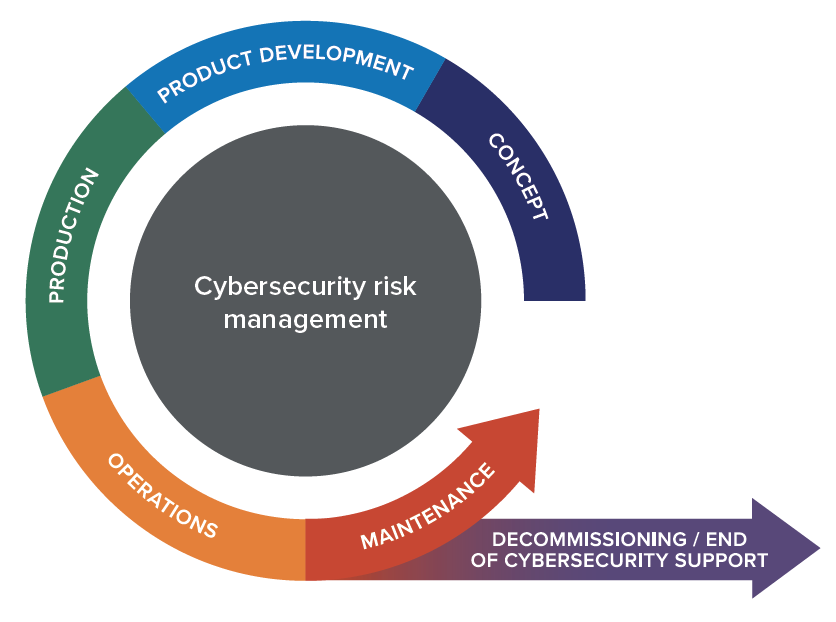
Lifecycle
ISO 21434 defines a cybersecurity lifecycle that starts with the definition of a new vehicle system and ends with that vehicle system being decommissioned or support by the OEM ending.
This means that cybersecurity activities continue after a system is put into production to ensure that new vulnerabilities that are discovered after a system enters production are still identified and mitigations added if necessary.
RELATED: The Impact of ISO 26262 on Automotive Development
Cybersecurity Management According to ISO 21434
Organizational
ISO 21434 defines requirements for an entire organization developing automotive systems to ensure that the necessary cybersecurity governance and culture are in place to support cybersecurity engineering. This includes ensuring that the organization acknowledges that there are cybersecurity risks, executive management is committed to the management of the risks, and that the organization has defined rules and processes to implement the requirements of ISO 21434.
In addition, the organization must have personnel in cybersecurity roles that are competent, policies that define how information can be shared both internally and externally, an appropriate quality management system, management of all product development tools, and robust information security. Audits must be performed to ensure that the organization achieves the objectives.
Project-Specific
Each project that develops or updates a road vehicle system or component must manage the cybersecurity engineering activities specific to that project. This includes the following considerations:
a) Assigning the responsibilities regarding the project’s cybersecurity activities to specific individuals
b) Planning the cybersecurity activities that will be performed during the project
c) Creating a cybersecurity case that provides the argument for the cybersecurity of the system or component
d) Performing a cybersecurity assessment if the project risks deem it necessary
e) A decision of whether the system or component can be released for post-development from a cybersecurity perspective.