Collaboration in product development helps improve quality, reduce risk and speed up development. For this reason, Jama Connect™ has context-based, actionable collaboration built into the platform. Reviews are a formal, effective collaboration method that guides teams in fulfilling regulatory requirements.
Our customers use these capabilities to collaborate with external stakeholders. For instance, Jama allows you to invite reviewers simply by email (Jama licenses include more than enough reviewer licenses for this purpose). This works extremely well in practice. In fact, one medical device developer, RBC Medical Innovations, was able to shed hundreds of team-member days during development to save $150,000 in cost savings per project.
Firewalls, Policies and Processes are Preventing Collaboration
One concern that many organizations have is IT security. In order to collaborate with external stakeholders, your Jama instance must be made accessible on the internet, or at least shared with collaborators via a secure connection (e.g., a VPN). Even if this is possible, decision-makers may have concerns — justified or not — about IT security.
Further, the other party (i.e., supplier or customer) must be willing to accept Jama as a collaboration platform. As such, the same concerns around security must be addressed on their end.
Lastly, even if all parties are interested in collaboration, one of them has an advantage: the one who has chosen Jama Connect as the collaboration platform. After all, that party not only gets collaboration, but also takes advantage of the complete Jama platform for end-to-end traceability, workflows and many more capabilities. The other party – the supplier or customer – can only collaborate on the content that has been made accessible.
The Alternative: Controlled Data Exchange via ReqIF
Data exchange between organizations is nothing new, and many organizations have collaborated for decades, typically by exchanging documents. While this approach technically works, it results in unstructured data that provides no traceability, no understanding of changes between versions and no easy way to provide structured feedback.
The automotive industry, traditionally working with hundreds of suppliers, has been a pioneer in this space. It’s not unusual to find tens of thousands of requirements in an automotive specification, so managing these requirements is a challenge. In response, the industry developed an international standard for the lossless exchange of requirements called Requirements Interchange Format (ReqIF). The standard was finalized in 2011 and has proven so popular that every requirements management tool today, including Jama Connect, supports it.
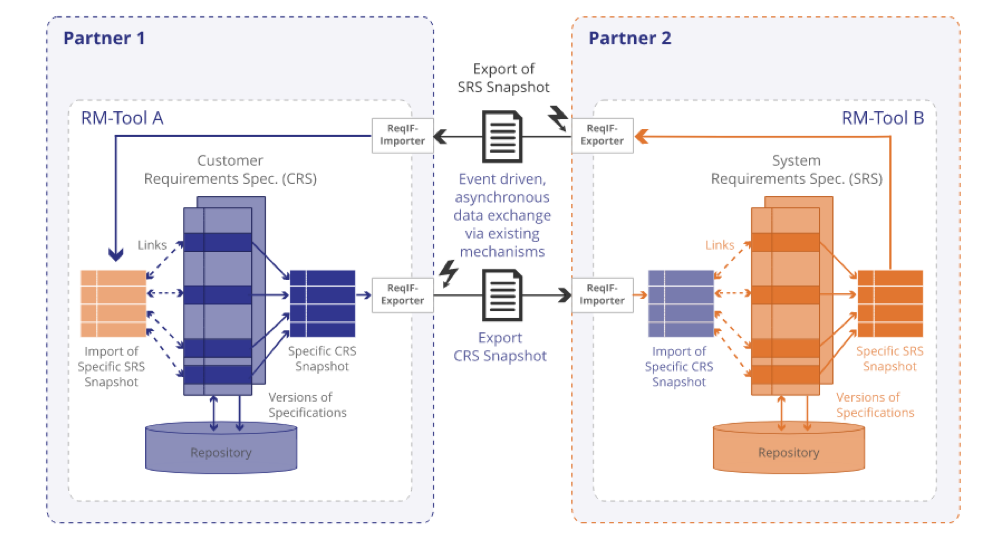
A requirements exchange with ReqIF has some similarities to the old (and dreaded) document exchange process: One party exports a ReqIF file and hands it to the other party. The transfer can happen via a portal upload, automated exchange or even as an email attachment.
But here’s where the similarities end: A ReqIF file contains structured requirements data consisting of individual requirements with visibility into structure, attributes, related elements and traces. It is loss-less: The data and structures that you see in your product development environment (like Jama Connect) stay completely intact.
ReqIF also supports incremental updates. If one party creates another version and exports a month later, you could import that version into your environment and the tool would show you clearly which elements, attributes and traces have changed. For instance, you could use suspect links to re-validate only those items that have changed.
Collaboration via ReqIF
ReqIF is commonly used to solicit feedback from a supplier. A producer could export the requirements for a supplier, including attributes for providing status feedback and comments. The supplier would then import the ReqIF file into the tool of their choice, where they could fill out the supplier attributes and send the resulting export back.
In addition, they could start integrating the imported requirements into their own development system. For example, they could establish traceability from the customer requirements through to design while keeping the process invisible to their customer.
Image Source: IREB Magazine
There are other use cases that ReqIF supports as well, but for all of them, the foundation is a controlled asynchronous exchange of structured requirements that keeps individual items, attributes and traces intact.
What about OSLC?
When talking about ReqIF, Open Services for Lifecycle Collaboration (OSLC) is often mentioned as well. This is another standard, but one for connecting product development tools. It has some similarities to Jama’s REST API, in the sense that OSLC is also an API for connecting tools. While the REST API supports all activities of Jama Connect, OSLC only supports a small set of activities related to requirements. But since it’s standardized, many tools provide out-of-the-box adapters, including Jama Connect.
However, OSLC is not the answer to enabling cross-organizational collaboration between teams, suppliers and customers.
Bottom Line: How to Collaborate?
If you are using Jama Connect, the built-in collaboration capabilities are the most effective way to work together.
However, if you are working with people outside your organization, your customers and suppliers may not be able to collaborate using your Jama instance. In those cases, a ReqIF-based collaboration could be a great alternative.
Learn more about the benefits of upgrading your requirements management process with our paper, “Getting the Most from a Requirements Management Tool.”