With President Biden signing the new Executive Order on Improving the Nations’ Cybersecurity. I thought it would be worthwhile explaining how Jama Connect can be used by both Cloud Service Providers (CSPs) and Third Party Assessment Organizations (3PAO) to accelerate and automate development of FedRAMP compliant and authorized offerings.
For those unfamiliar with FedRAMP, it is the US Government’s cybersecurity framework for commercial IaaS, PaaS, and SaaS providers which, if successful, allows those CSPs to deliver cloud based services to federal agencies. Historically, all federal applications had to be hosted within federal controlled data centers, and FedRAMP enables delivery from CSP controlled commercial infrastructures. Each of the major cloud infrastructure providers have FedRAMP approved environments, and thus, PaaS or SaaS companies can leverage similar environments to their existing commercial applications for FedRAMP.
The cornerstone of FedRAMP is the System Security Plan (SSP). The SSP is the documentation package to basically describes how the CSP has developed the system in compliance with the required security controls, and how the CSP will operate the system in a compliant manner with the requirements. The SSP is interesting because it simultaneously documents the requirements and the technical/operational design of the system.
Depending on the complexity of the system, the SSP package may be 400-1500 pages when printed. This is not something that you print out and expect people to read. However, this is what the 3PAO and the FedRAMP Sponsor (the federal agency taking you through the process) read in detail to determine compliance and to understand the risks associated with accepting the system as developed, or if additional security measures are required.
One of the huge challenges with FedRAMP is to get today’s DevOps teams to not only read the requirements, but to also design/implement the system in accordance with the requirements and to participate in the necessary documentation of how they built the system. Having tried to just shove a very large Word document at them in the past, I’ll testify that approach is one to guarantee failure. In reality you’ll have a small team with someone like me on it, coordinating FedRAMP requirements decomposition, writing documentation, and closely working with the DevOps team to ensure that they 1) understand the requirements, and 2) the documentation accurately represents the implementation.
If you have made it this far in my blog post, I hope you have a sense of the complexities and the requirements/documentation challenges with FedRAMP. But since this blog is on Jama Software’s website, I should pivot slightly and explain how Jama Connect can make FedRAMP much easier. While there are several tools available that will help you write an SSP, most of those tools are not fully developed requirements management tools, and as such do not allow for flexible approaches, customization, requirements decomposition and tracking, flexible workflow, and so on. I have found it better to adapt Jama Connect to work with FedRAMP, than to take other tools and try to make them into requirements management tools. It is a tradeoff, and Jama Connect does not currently generate an SSP at the push of a button, but that isn’t as important as getting the requirements right the first time and getting into the market and generating revenue.
RELATED POST: Checklist: Selecting a Requirements Management Tool
So, what can Jama Connect do for you if you are getting into FedRAMP?
- Jama Connect can be your reference library so you can avoid hunting for documents on the internet
- Jama Connect can provide valuable guidance on the best practices regarding FedRAMP development
- Jama Connect can be used to actually develop the SSP, and to then create and track the required product feature requirements or tasks to ensure that system is built and operated in a compliant manner
- Jama Connect can be used to share the SSP artifacts with the 3PAO and to get their feedback
- Jama Connect can be used to identify and collect the evidence required for the audit
- Jama Connect can be used to identify and collect the evidence required for continuous monitoring
I’ve created a very barebones sample Jama Connect project to explain some of these capabilities in more detail. Most of the effort in building this was uploading the NIST controls from a spreadsheet and building out the organization based on my experiences.
Before jumping into screenshots and so on, it has also been my experience that not everyone on the FedRAMP team, especially those team members in DevOps will want to use Jama Connect. While it may be impossible to fully collaborate with them without having them at least occasionally go into Jama Connect, there are two Jama Connect features worth addressing. The first is that it can integrate with multiple existing DevOps tools, so tasks in Jama Connect can show up as tickets in Jira and etc. This allows DevOps to continue to operate in the tools they are used to, yet the overall FedRAMP effort to be managed and documented in Jama Connect. The second feature is that if I make a comment in Jama Connect and I tag another user, then Jama Connect can send that user an email. That user can then respond by email. This is two ways that non-core team members can effectively participate with the team without needing to be Jama Connect experts.
Now, for this demo project, I’ve assumed that the entire team is able and willing to work within Jama Connect. Hopefully this will help describe the scope of work necessary for FedRAMP and how Jama Connect can be that one central working space to manage the required FedRAMP requirements and documentation.
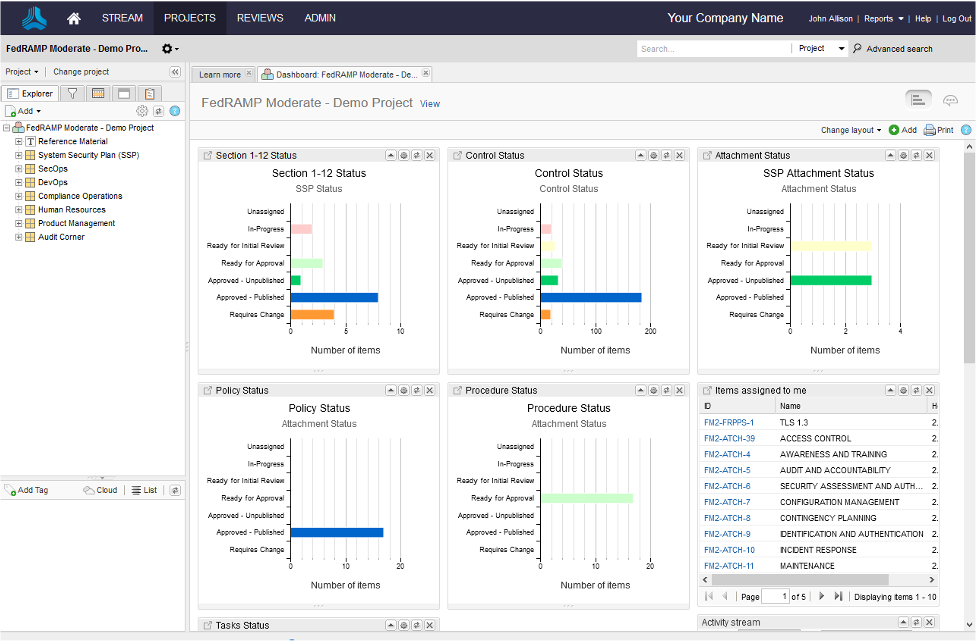
Let’s start by looking at the Jama Connect dashboard for my sample project.
The ability to actually track the status of every piece of required documentation and each of the security controls is why you never want to just build an SSP package in Word or Google Docs. At one glance I can see where we are in getting the SSP completed, and how we are doing with each control. I can also see everything that is assigned specifically to me, so I can click on any one of those links and start editing.
The SSP package is complex and if you do it right, you’ll have multiple authors, reviewers, and so on. If I was the sole person responsible for building the entire package then I wouldn’t need Jama Connect and my company would fail. FedRAMP is a team sport, and the dashboard is your game plan.
The beauty of this is that unlike other tools that allow you build the documentation, Jama Connect can be configured to track anything. So, if there are specific product feature requests that must be met to be compliant, that too can be included in the dashboard. The same goes for all of those DevOps tickets that are used to facilitate building the actual system.
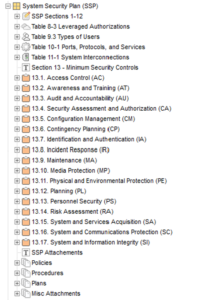
Let’s take a closer look at the SSP itself.
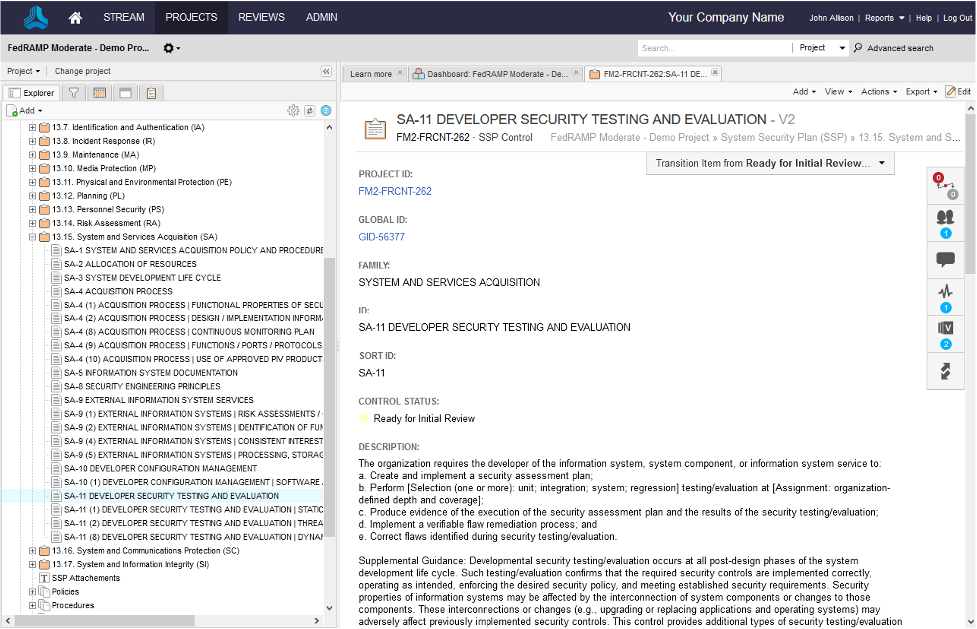
This is what an SSP looks like in Jama Connect, or at least the outline of an SSP. Now, the new cybersecurity Executive Order goes into detail on the requirements for improved secure development practices, so let’s jump into SA-11, Developer Security Testing and Evaluation.
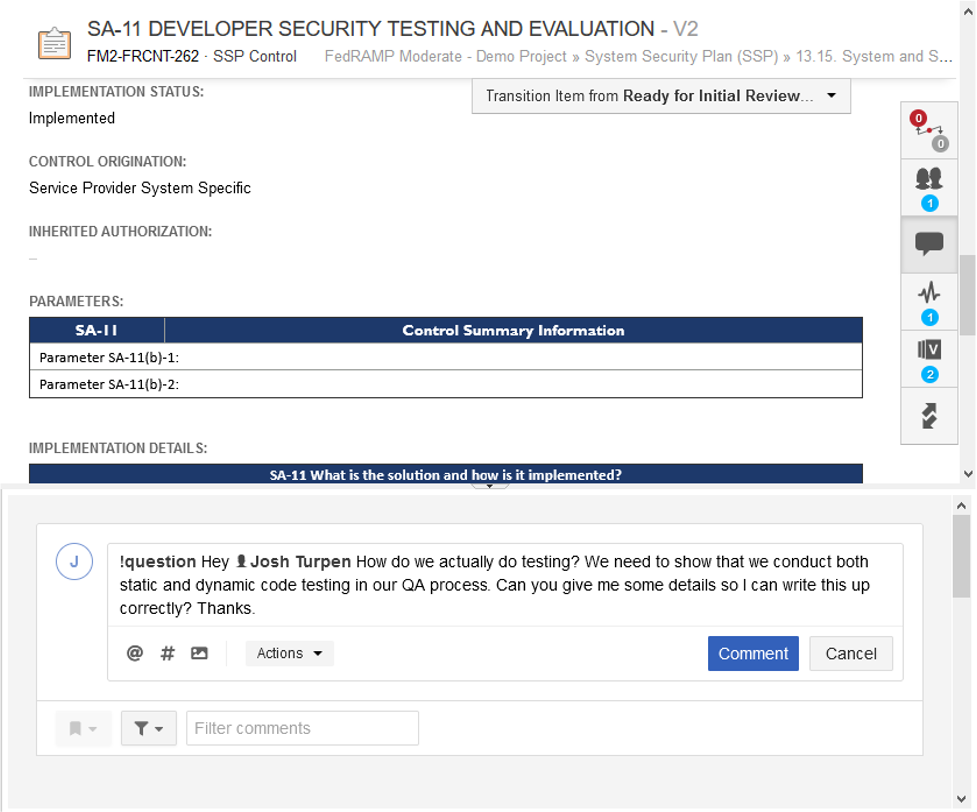
For the demo project, I’ve included the NIST and FedRAMP guidance for each control with the response. Now, if we scroll down a bit.
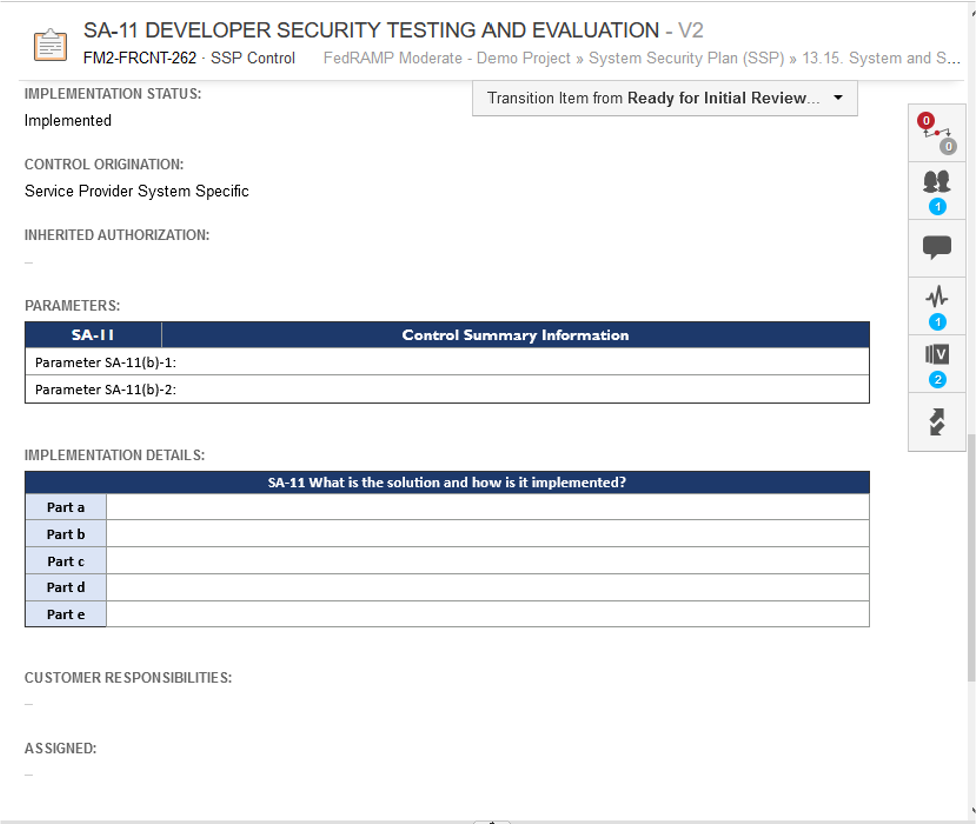
Below the guidance, are the fields that the CSP must fill out and be audited against. This is where someone like me would start writing. However, if I do not know how we do testing, I can use Jama Connect to start asking questions.
I can ask Josh for details on this. He can answer by logging into Jama Connect or simply by responding to the email. Jama Connect will track unanswered questions so you can blast out questions and not get lost in the responses. Try doing that in Google Docs or email. Josh can also just click on the link in the email and then see the requirements or any of the documentation stored in Jama Connect.
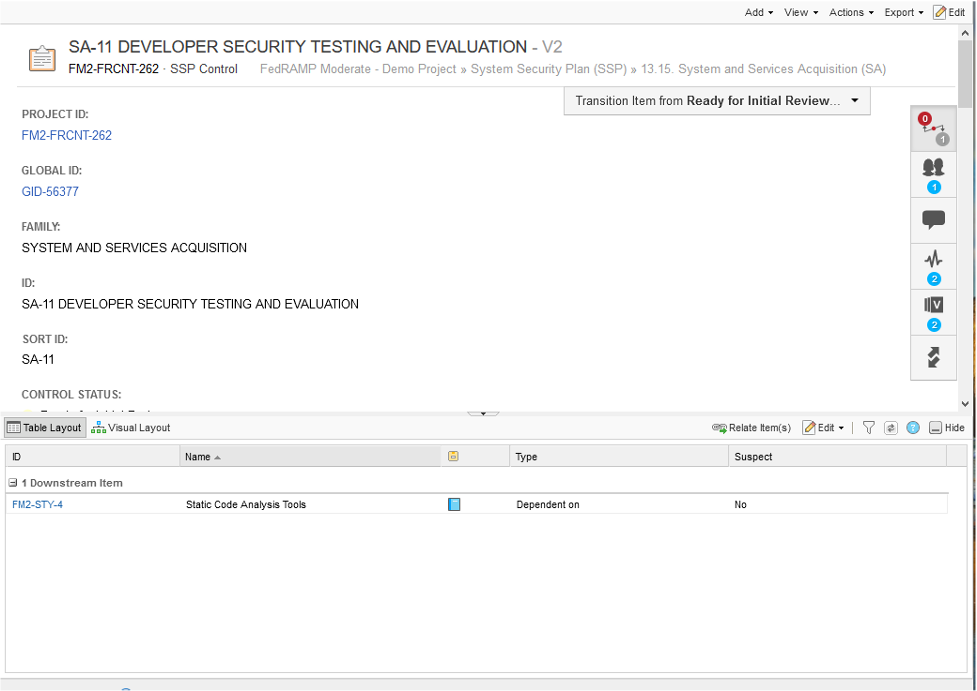
Unfortunately Josh responds with “Ummm we don’t do this,” so now we need to create a DevOps user-story to get them to install the appropriate static code analysis tools. Easily done in Jama and now we have both the control, and a related user-story.
Now, I can track the completion of the user stories or tasks that must be accomplished to either make what is written in the SSP true.
So, Jama Connect can be used to build your SSP package and to assign user-stories/tasks as required across your company to either complete the SSP, or bring what is said in the SSP into reality. If it can do this, and your teams can effectively use Jama Connect for this, it has already paid for itself (at least in my opinion).
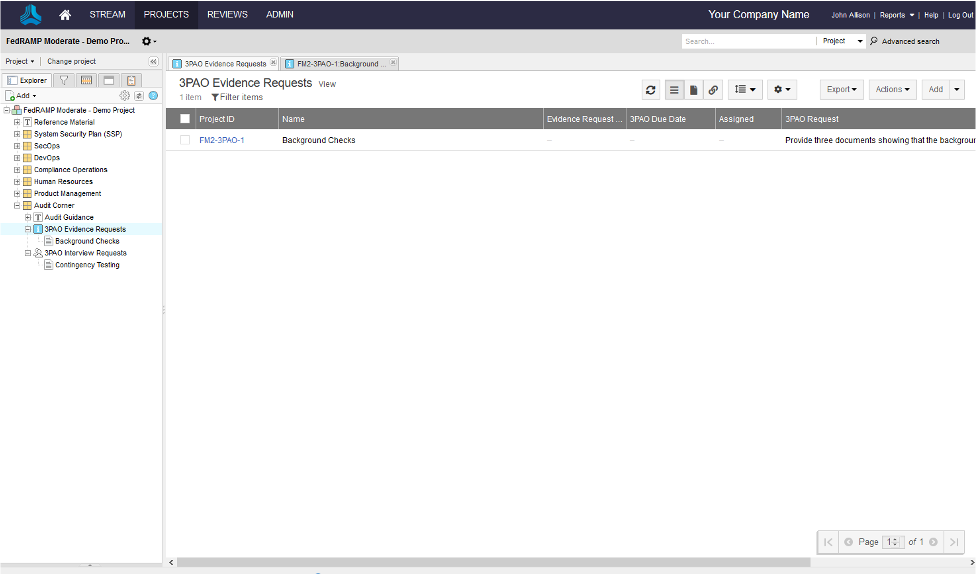
When you get the SSP complete and your Sponsor approves the System Assessment Plan, it is time to go into audit. For the audit, the 3PAO will provide you a list of all of the evidence required, which generally is either documentation, interviews, or a demonstration. The CSP then has to provide the documentation, schedule the interviews and conduct the demonstrations. This can also be facilitated by Jama Connect. Some 3PAO’s have their own online tools for this, and some will just send you a spreadsheet. The good news is that you pay them, and if you’d like them to submit and track the audit completion in Jama Connect, that may be doable depending on the 3PAO.
Above I have just a simple evidence request on background checks. It is easy enough to give the 3PAO access to Jama and for them to upload their evidence requirements. Then the CSP can attach the evidence to the requirements and the 3PAO can review and approve the evidence submission. This is easy to do in Jama through component level permissions (you don’t want the 3PAO going through everything in Jama) and workflow. This can then be added to the dashboard so you have a near real time assessment of how the audit is going.
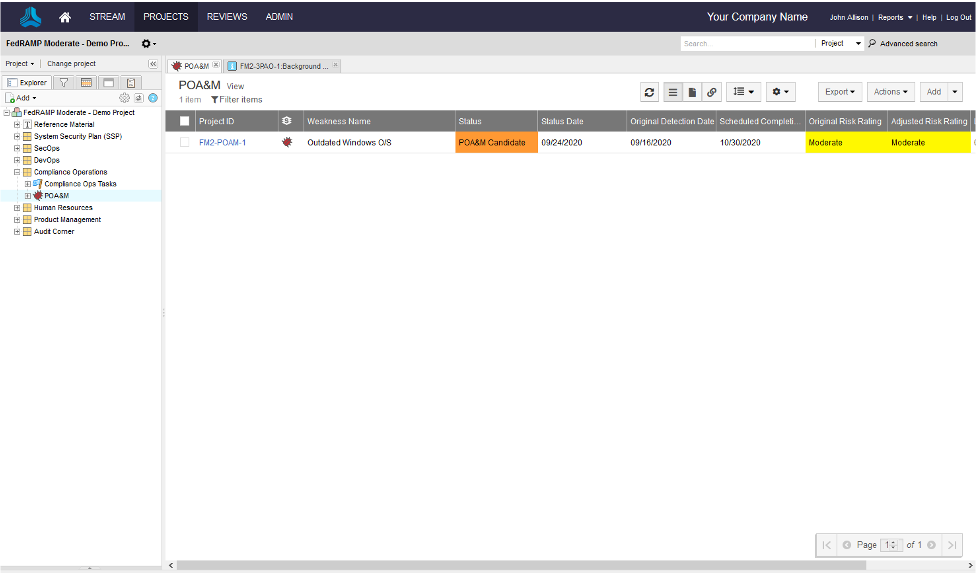
The last aspect of Jama Connect I want to share with you is continuous monitoring, and the Plan of Actions and Milestones (POA&M) specifically. After you survive the audit and get your authorization, you enter into continuous monitoring. One important part of that is establishing and maintaining the POA&M, which is where the CSP documents the risks associated with the system and the plan associated with mitigating the risks. The POA&M is provided to the government monthly. While there are other tools designed specifically for POA&M management, again those are niche IT spends and aren’t suited for requirements decomposition and task assignment.
Above is one simple POA&M item. Normally a CSP may be monitoring between 50 and 200 POA&M items at one time. Just like the controls, Jama Connect allows you to fully document the POA&M and then to create related user-stories or tasks, and then track those to completion. It also allows you to start tracking items that may not yet be on the POA&M, but that if are not remediated within the required timeframe will be put on the POA&M. Again, just like everything else with Jama Connect, how the POA&M field types are configured and the workflow is all customizable, so it can be adapted to what works best within the CSP.
In summary, Jama Connect can be a critical tool if used correctly for any CSP desiring to get into the FedRAMP business. Jama Connect’s flexibility, collaboration capabilities, and ability to integrate with all existing tasking tools can significantly streamline SSP development, audit preparation, and support the successful completion of the audit. The effectiveness of Jama Connect in FedRAMP is completely dependent on the CSP’s willingness to leverage it, and there is nothing about Jama Connect from a capabilities standpoint that restricts it’s effectiveness. While it may not offer the one-button SSP generation solution that niche SSP tools may offer, the benefits of Jama Connect significantly outweigh the few hours of effort to build the SSP in Word for the PMO.
And while the perfect solution for this does not exist, Jama Connect does break the requirements and development out of an unreadable Word document and into the light, where the entire CSP can focus their efforts to achieve FedRAMP authorization in the most efficient manner possible.
Stay tuned for John Allion’s 8-part series on how Jama Connect supports government program offices and read the series introduction here.